IoT (Internet of Things): Building Scalable IoT Architectures
-
Caploitte
-
24 March 2024
-
05 Min Read
Introduction to IoT (Internet of Things)
Principles listed
Scaling IoT on Other Devices
Development service APIs
Quality in IoT Platforms
M2M Communication Styles
Scale with Simplicity
Conclusion
Introduction to IoT (Internet of Things)
What does it mean to have data as your guide? In today’s world, data-driven engineering and commercial solutions are becoming standard. Just a few centuries ago, data collection procedures included manual counting and calculating, which at the time was associated with computing. The scalability of this manual labor was clearly problematic.
A new era in computing was ushered in with the invention of the difference engine, or automated mechanical calculator, in the 19th century. Early attempts to construct workable mechanical automata encountered significant difficulties, leading to the abandonment of the mechanical strategy in favor of an electrical one. The main objective in both situations was to increase computer power. Without data, computing is worthless, thus data and computing nodes must be connected in some way. Data may now come from anywhere thanks to recent developments in communication technology, particularly the internet’s rise. This strongly shifted our focus toward distributed solutions in terms of data storage capacity, reliability, scalability, and performance.
However, the limited processing capacity found in big data centers is insufficient to manage the volume of data that is growing every day. In cases of such a situation, the network would create an obstacle for data transfer. The goal of ubiquitous computing, also known as pervasive computing, is to integrate computer power into end devices, which are typically also data sources. The idea of executing computation anywhere, ideally close to data which is also associated with edge computing creates new opportunities for data processing. Our quest for encompassing the greatest amount of data inspires creative, scalable IoT solutions in our thinking.
The axiom that “more data equals bigger potential to discover new facts and expand knowledge” is a simple one to understand. Naturally, the volume of data necessitates more intricate and effective calculations. Getting a competitive edge in a company or research is the main objective. An infinite cycle of data-driven computing is depicted, where data are the raw materials and computation is the goal-oriented process of synthesizing higher-level insights.
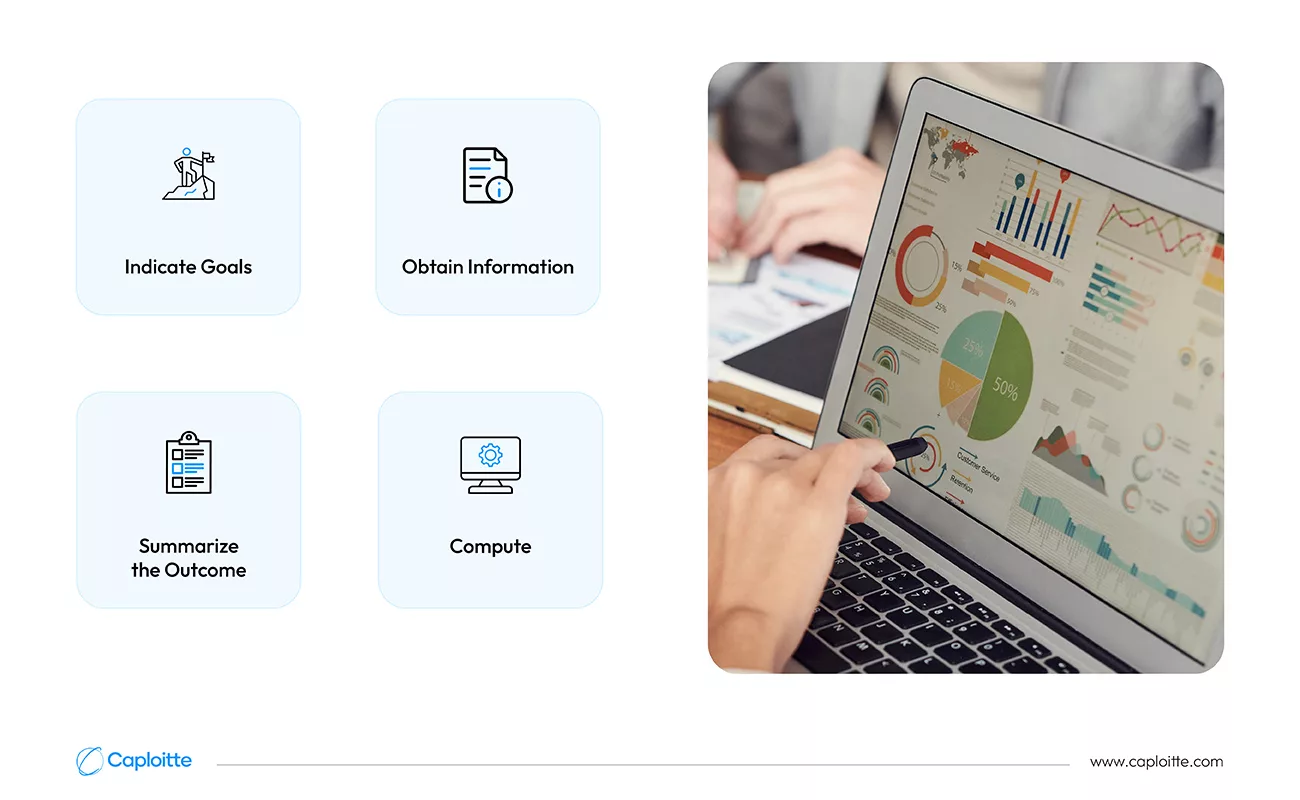
Indicate goals
Use cases must guide data handling and collecting. It cannot occur by accident when listening to every type of data source and compiling records. The purpose of the data should be evident and provide context for the calculation involved. A machine controlled by artificial intelligence or a person can do this planning step.
Obtain information
The collection of data must be efficient in terms of both time and resources. It must also be technically possible and produce data that is appropriate in quality. A proposal for a workable data serialization format, an analysis of the necessary data transformations, and a specification of the requisite communication routes and protocols must all be included in the data collection attempt. As a sort of feasibility assessment, many of these factors ought to have been taken into account at the earlier planning stage.
Compute
This is the process of crunching data, where several programs are applied to the gathered information. Reporting tools, machine learning resources, data transformation pipelines, and similar applications could be part of the suite of programs. Usually, the result is a fresh collection of data that accurately encodes the combined knowledge.
Summarize the outcome
The additional information that was discovered by doing the earlier computation should prompt the necessary activities and result in plans that may have higher expectations. This is the last stage before a new cycle, powered by the output of the previous one, starts.
The well-known principles listed are essential to every data mining project
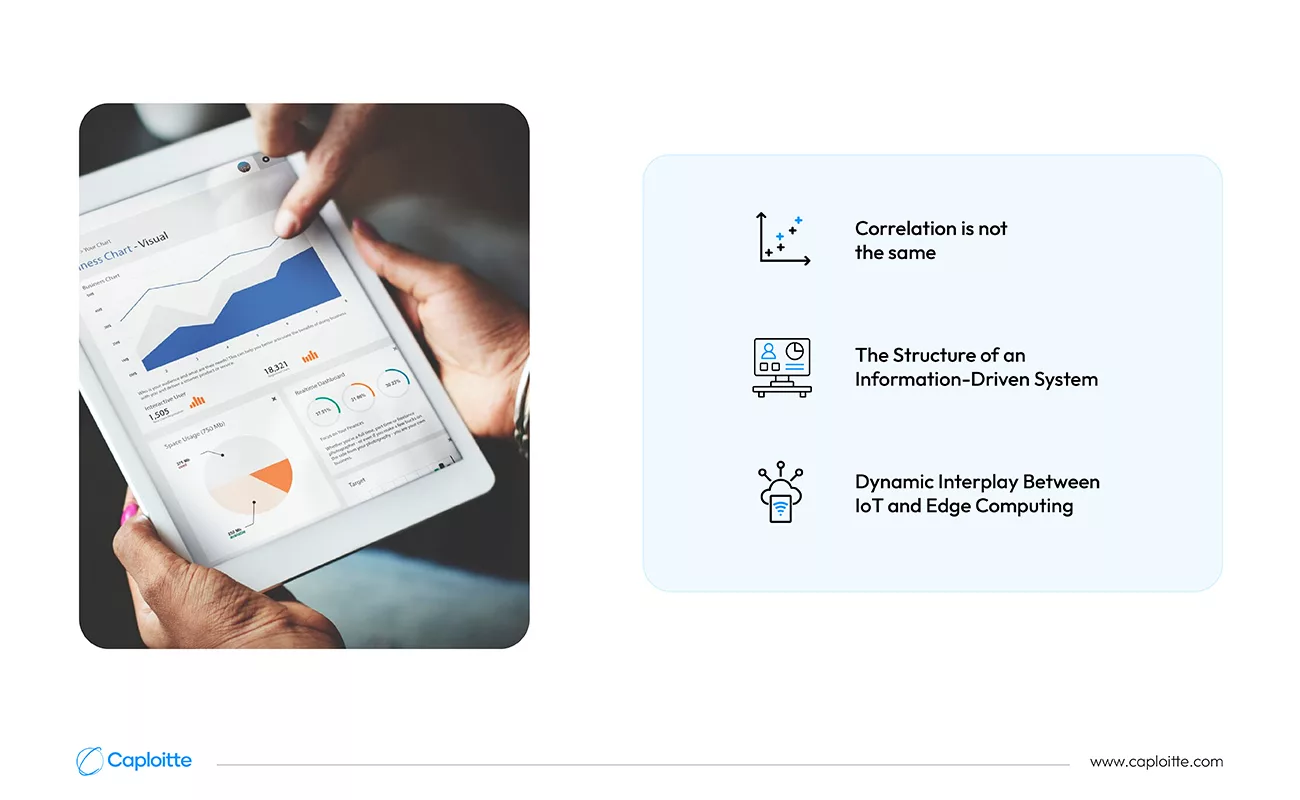
1. Correlation is not the same
Finding patterns in data will help us realize the benefits of leveraging the data-driven inference cycle. These patterns typically point to important connections between the objects or events that the data represents. Carrying out large-scale data analysis without understanding the risks associated with concluding too soon might cause more harm than good. Many instances of how things might go wrong can be found online some of the most embarrassing errors were even committed by data scientists. It does not follow that someone with larger feet is necessarily smarter than someone with smaller feet, for instance, even if there is a link between shoe sizes and intellect. In this instance, the model does not include age as a latent variable.
2. The Structure of an Information-Driven System
Any software system that is driven by data must have a strong architecture. The design combines important system quality criteria in one package and enables system analysis before system construction. It is crucial to include technology issues early in the design when data-driven computing takes on cutting-edge technologies. A possible strategy for creating a suitable design of this kind may center on the design Tradeoff Analysis Method. The tradeoff Analysis Method integrates a quality characteristic and technology analysis.
3. Dynamic Interplay Between IoT and Edge Computing
To implement the data-driven computing paradigm, the Internet of Things (IoT) integrates devices, connectivity, platforms for data collecting and processing, and bespoke applications. By delivering computation close to data rather than centralizing everything in one place, edge computing is a strategy typically a cloud-based data center.
This effectively demonstrates how an IoT (Internet of Things) platform handles devices on the left and enables services on the right. The bidirectional arrow denotes the degree of accomplished computational spread as well as the communication pathways between layers. If the boundary lies far to the left, this means that intelligent, self-governing gadgets—such as smartphones—must possess sufficient processing power to execute intricate programs. On the other hand, the devices are merely dumb data sources that relay data to and from applications through intermediate hubs. This scenario is similar to a remote database file hiding on a file server in a desktop database program like the one used in Microsoft Access, for instance. A routine query will initiate unnecessary network data transfers; this method is not scalable.
A device can serve as a data source, data processor, or data sink in addition to these three tasks individually. Devices might function alone or collaborate to create a dynamic mesh network. A swarm of devices is a collection of devices that behave following both the overall goal and the actions or states of its neighbors.
The main function of an IoT platform is to create the data segment and process it into a single, cohesive part. The Internet of Things platform can run in the cloud or on-site. The following are the main duties of the platform:
– Enables bindings for communication between devices
– Applies the rules engine for response processing and data segmentation
– Retains both transient and permanent data, runs several analyses, and produces reports
– Provides access to administration, oversight, interoperability, and bespoke application
Scaling IoT on Other Devices
Use a standard API for both web and mobile apps to reduce redundant code.
1. Use separate systems called web workers for data storage and analysis with a dynamically growing pool.
2. Make the communication stack from the end devices to the cloud asynchronous to reduce load times.
3. Consider edge computing and fog computing to distribute computational tasks to servers at the edge or intermediate stages.
4. Use concurrency to perform multiple tasks simultaneously with shared resources.
Development service APIs

A language unique to a certain domain may be used by the rules engine to express condition-action connections. Either specified rules or rules that are self-managed by machine learning algorithms are possible. Events (messages) coming on separate communication channels may have varied priorities, meanings, and reaction times; rules may also control the categorization and routing of input data.
It is possible to join many IoT systems together to share data. Applications developed on top of these networked IoT systems may make use of data affinities and merge data from several areas.
Using an IoT platform’s advertised services, a bespoke IoT application may concentrate on business use cases rather than device administration and raw data processing. Applications are divided into verticals, each of which focuses on the corresponding domain of autonomous cars, smart grid, healthcare, agriculture, etc. It is crucial to keep in mind that a single data channel may simultaneously engage in several sectors. For instance, there are several applications for weather forecast data. Moreover, distinct data may be sent by the same device for many verticals. Many healthcare apps may use a smartphone as a data source, and it can even run other unrelated IoT applications concurrently.
Given that a data-driven system might have many deployments, this makes sense. To handle as much data locally as feasible, an IoT platform, for instance, may be hosted by a capable device. It is also possible to combine apps on the same PC with an IoT platform. Nonetheless, the important thing to remember is that components should be conceptually and physically coupled in an effective manner. This goal must be supported by the deployment scenario. The easiest way to express the merit is probably to use a variation of Metcalfe’s rule, which says that the value of a networked solution like this is equal to the square of all of its linked elements.
As of right now, Ignite and IoT Methodology are the two IoT-specific formal development approaches that emphasize the value of architecture. The IoT OSI reference model is introduced in the IoT Methodology. Unlike the IP hourglass model, which has just four layers, it has five layers. Device, connection, middleware, services, and applications are at these levels.
Quality in IoT Platforms
An IoT platform’s quality goes beyond simply meeting stated requirements. It also needs to address unwritten needs and potential future demands. This means thinking beyond a narrow focus on functional requirements and embracing critical non-functional characteristics embodied in the system’s architecture. These characteristics, often referred to as “ilities,” like security, performance, and scalability, play a crucial role in delivering a good user experience and a robust system.
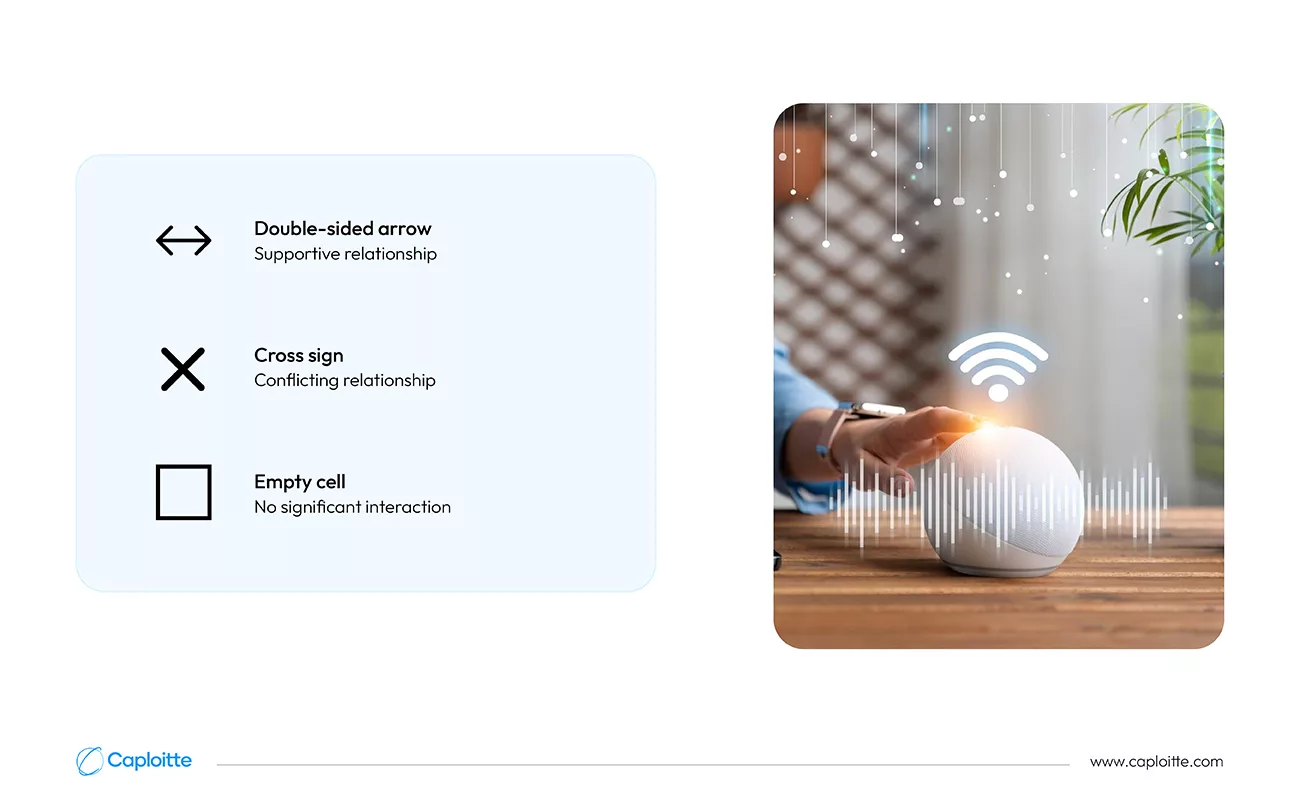
However, it’s crucial to understand that these characteristics interact with each other in complex ways. Some, like security and usability, often trade off against each other. This text uses a symbol guide to visualize these interactions:
- Double-sided arrow: Supportive relationship (e.g., reliability supporting security)
- Cross sign: Conflicting relationship (e.g., security restricting usability)
- Empty cell: No significant interaction
The text further categorizes these characteristics into user-visible (adaptability, usability, scalability) and internally visible (security, performance) to highlight their impact on different aspects of the platform. Notably, efficiency transcends both categories, being essential for both user experience and internal system operation.
In essence, this text emphasizes the need for a holistic approach to quality in IoT platforms, considering both stated and unstated requirements, the interaction between non-functional characteristics, and their impact on users and the system itself.
M2M Communication Styles
In the world of machine-to-machine (M2M) communication, two main conversation styles rule the scene: request/response and publish/subscribe. Choosing the right one for the job is key to unlocking swift responses, high reliability, and peak performance.
Request/Response: A Personalized Chat
Think of this like a one-on-one conversation. It’s perfect for targeted information exchanges, like a sensor requesting a security key or fetching its personalized schedule. But this style falters when you need to broadcast an event to trigger actions across multiple devices. Imagine telling dozens of friends the same news individually – not efficient!
Scaling Up with Publish/Subscribe: Group Chats Take Over
Imagine a group chat where one device publishes an event (like “temperature alert!”) and interested devices automatically subscribe and react. This is publish/subscribe in action, ideal for triggering mass actions without overwhelming a central hub.
Both styles have their limitations. Both can struggle with handling huge numbers of devices, and they sometimes have a single point of failure (like the central hub in publish/subscribe).
Solutions on the Horizon
While these communication patterns are essential tools, researchers are exploring ways to overcome their limitations. Future advancements promise even more robust and scalable ways for machines to chat and collaborate!
Scale with Simplicity
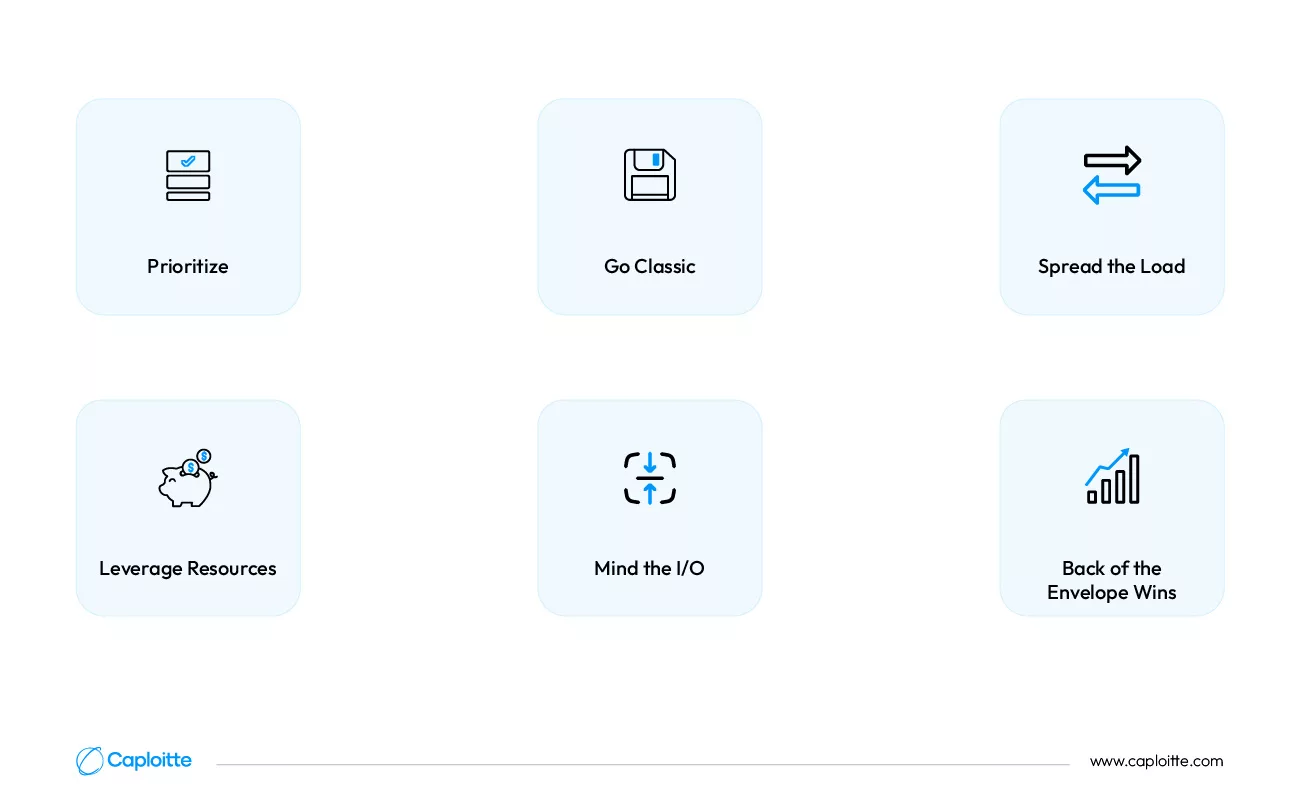
Prioritize: Scale design first, focusing on handling 5-10x user growth seamlessly.
Go Classic: Avoid bleeding-edge tech. Optimize for core tasks before adding bells and whistles.
Spread the Load: Use horizontal scaling (adding more machines) whenever possible.
Leverage Resources: Employ cost-effective tools like cloud, commodity hardware, and caching.
Mind the I/O: Reduce expensive input/output operations and transactions.
Back of the Envelope Wins: Estimate performance needs realistically before diving deep.
Conclusion
There is a limit to what the machines themselves can do to maintain their optimal and efficient performance, given how common Internet of Things (IoT) systems are expected to grow in the future. It is anticipated to play a key role in facilitating the integration of internet usage across a broader range of connected objects and gadgets.
Share this post:
Read More
- All
- AI
- AR
- DevOps and CI/CD
- E-commerce
- FinTech
- IoT
- Mobile Development
- Outstaffing
- Security
- SEO
- Tech Trends
- Web Design
- Web Development




