Security by Design: Integrating Security into the Development Lifecycle
-
Caploitte
-
28 April 2024
-
04 Min Read
The life cycle of software development
DevSecOps: What is it?
Using DevSecOps to Integrate Security Into the Application Lifecycle
How to Put Security Into the SDLC
Conclusion
Security by Design has become a primary concern and should be included from the beginning of the application lifecycle to reduce expenses, work, and complexity in the future. Functionality has always been the main priority in software development. Although there are a lot of approaches available to help with this, security is sometimes disregarded as an essential element. The public can access anything on the internet. That is the reality of our current digital age. If you don’t take certain precautions to guarantee security, anyone with bad intentions can quickly identify the holes in your goods and utilize them to get access to your systems. The life cycle of software development is not any different.
The life cycle of software development
The process of ideation, design, and eventual development of an application is known as the Software Development Life Cycle (SDLC). The Waterfall technique, Agile methodology, and Iterative approach are a few examples of SDLC frameworks. Every framework has a distinct structure and methodology, and companies often employ the one that best serves their sector.
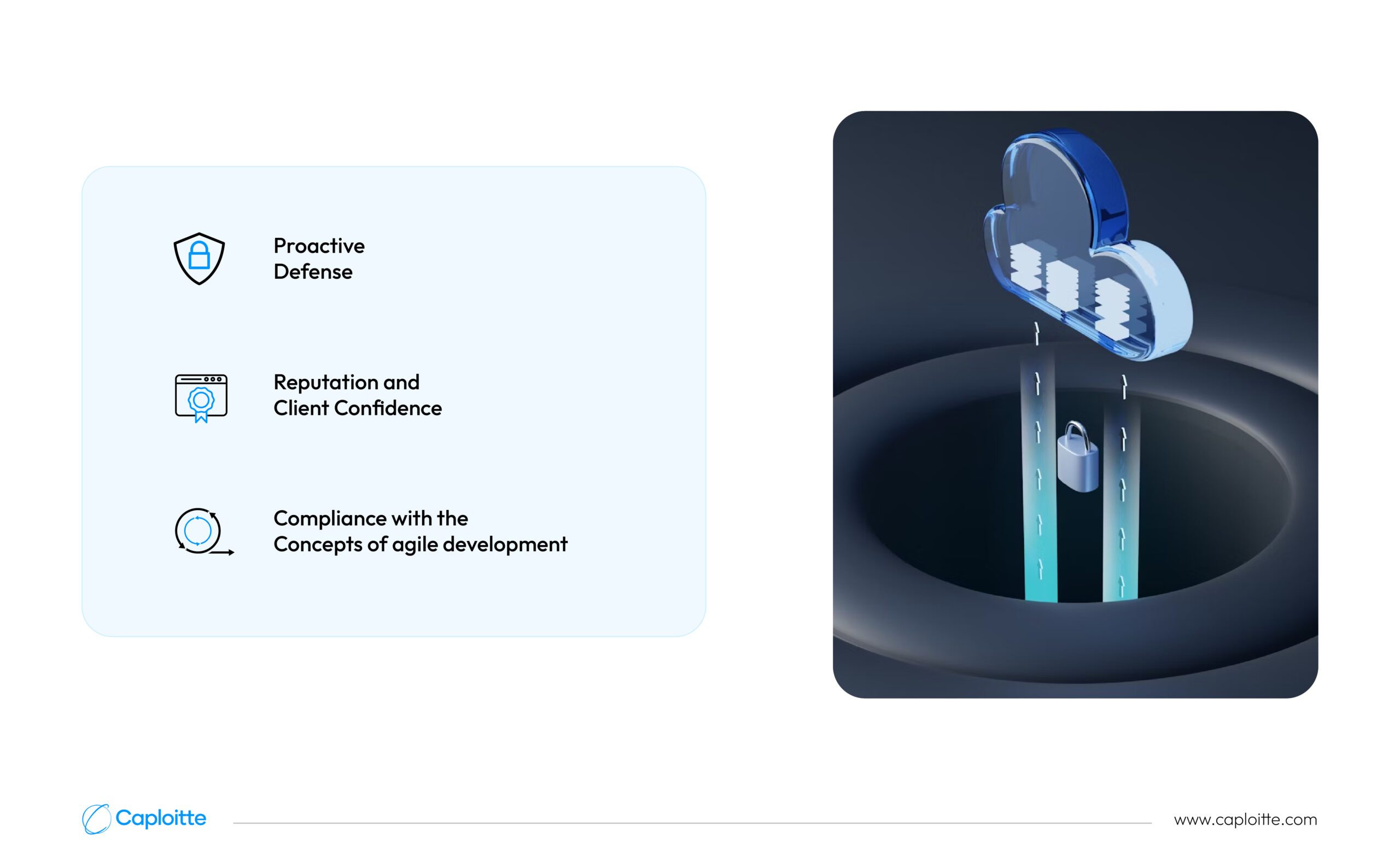
It is important to give security by design top priority in software development for three main reasons:
- Proactive defense. By including security by design from the outset, vulnerabilities are found and fixed before they are exploited. By being proactive, risks are reduced from the start.
- Reputation and client confidence. Sustaining consumer trust is contingent upon security. Users anticipate that their apps will be resistant to attacks and that their data will be secure. Investing in security by design early on helps establish a strong, long-lasting reputation.
- Compliance with the concepts of agile development. Agile concepts are aligned with the Development Lifecycle Integration when security measures are incorporated, resulting in quicker and safer deliverables. Instead of impeding growth, security helps create dependable and strong goods.
DevSecOps: What is it?
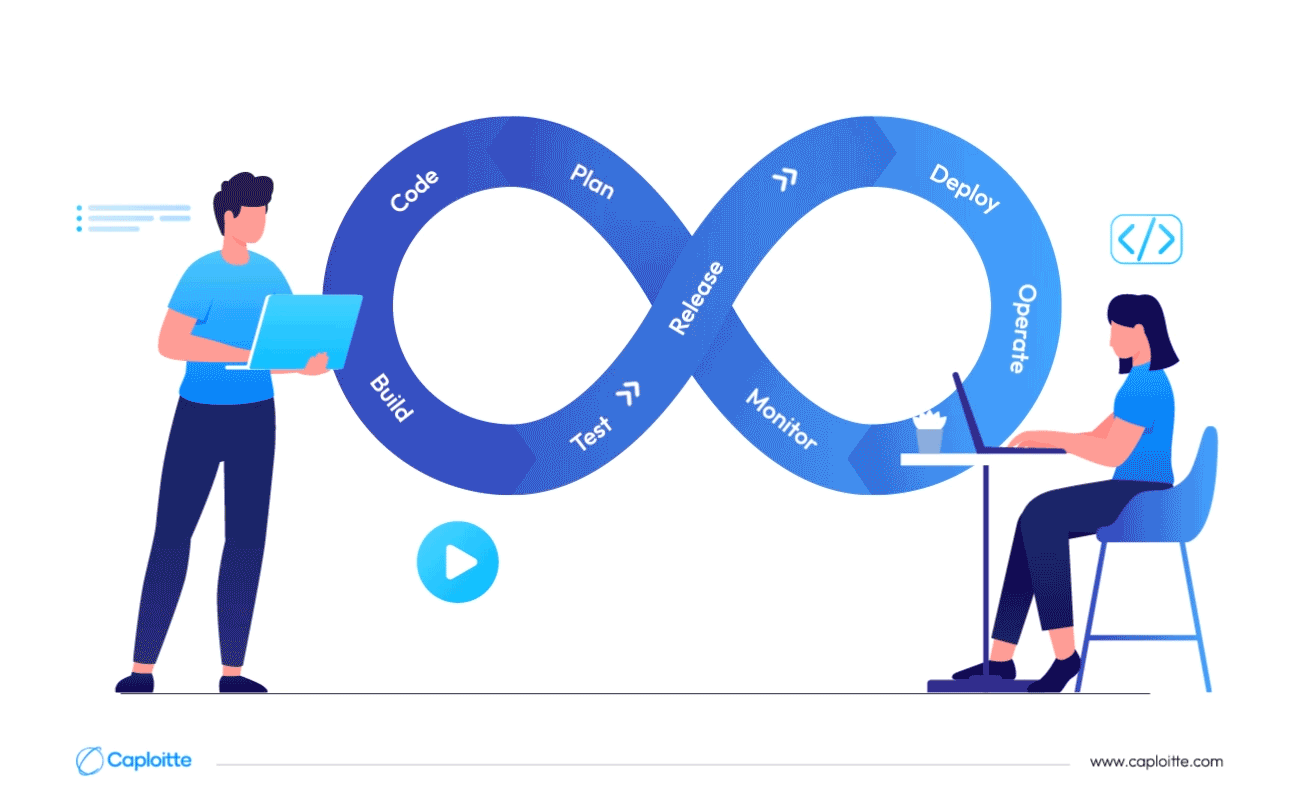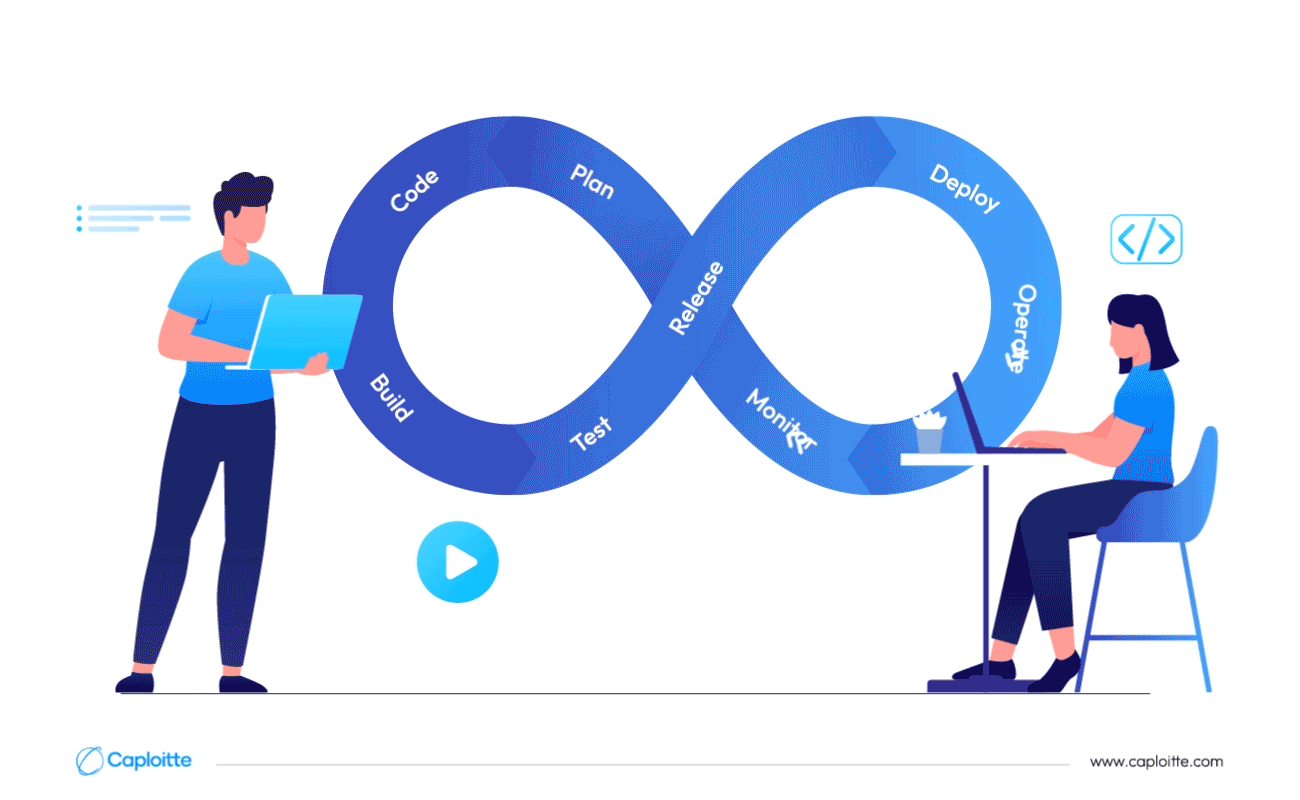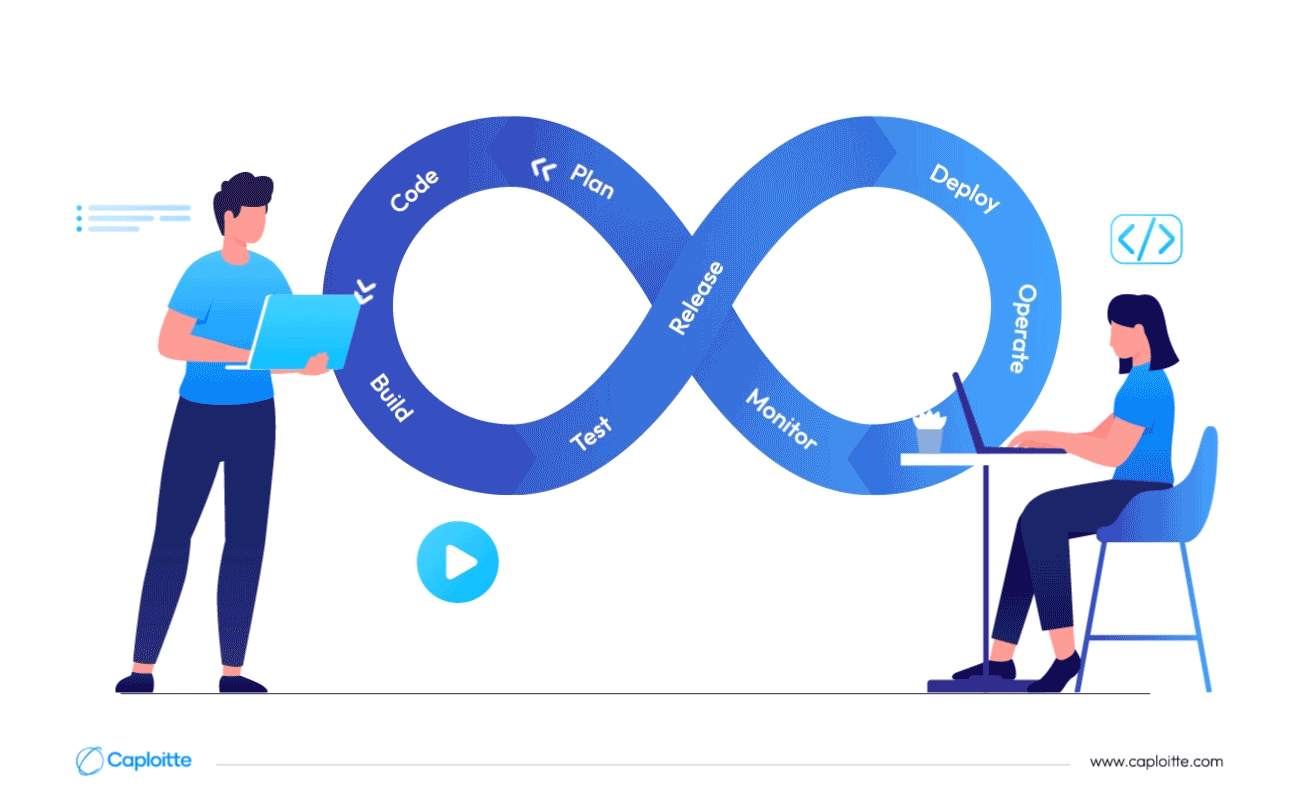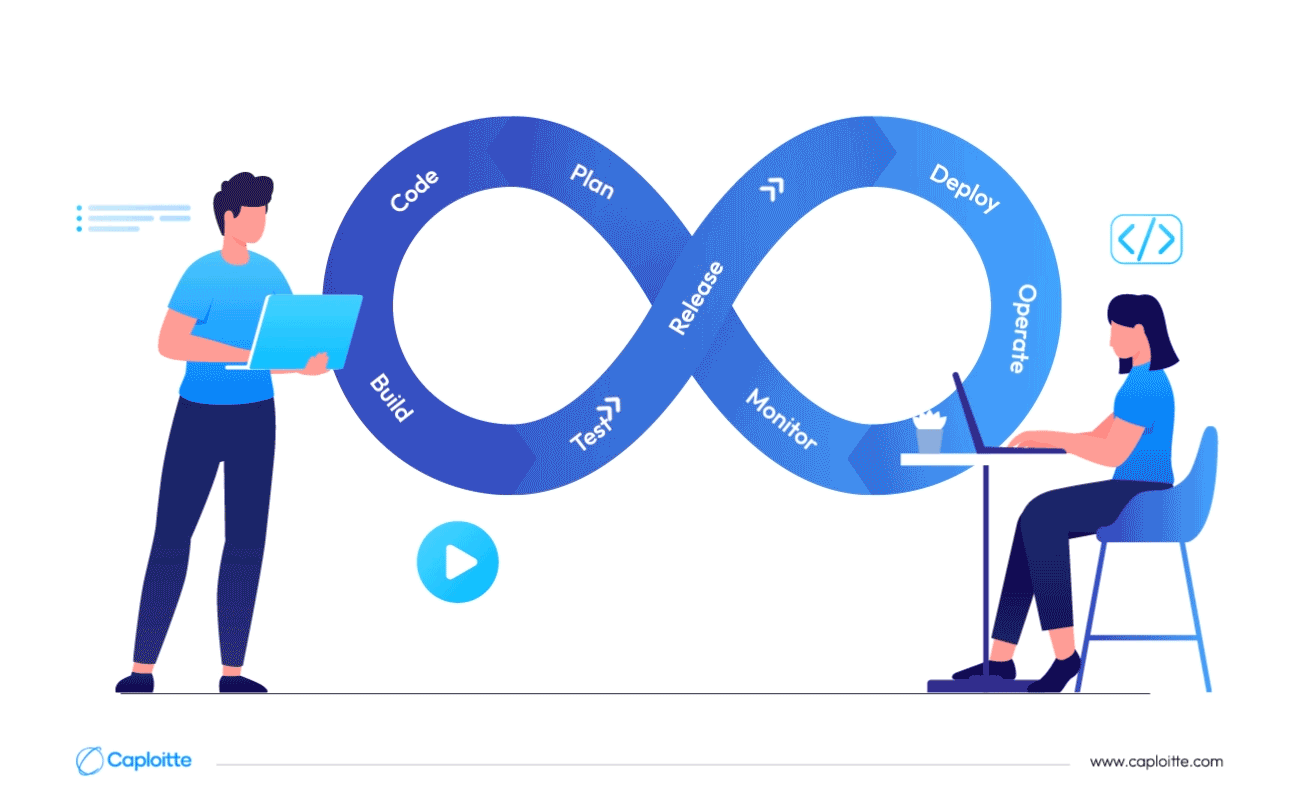
DevSecOps functions as an extension of DevOps by integrating security into both development and operations. Encouraging security-as-code ethics, this driving and monitoring SDLC approach imparts seamless flexibility to all stakeholders in the software development process.
Compared to the traditional DevOps methodology, DevSecOps guarantees that security functions in tandem with Agile and DevOps processes and expedites the release of code and products. Similar to how DevOps removed traditional boundaries between development and operations, its goal is to accomplish the same for security by design, operations, and development teams.
First, while maintaining the pace of development lifecycle integration operations, DevSecOps makes it clear that security is a responsibility of everyone.
Along with devoted security specialists, the DevSecOps concept promotes a collaborative framework that gives access to technologies and processes that facilitate security decision-making. By enabling the system to continually monitor, recognize, and resolve security concerns, it enhances its value. To put it briefly, security is a process that oversees each stage of development operations rather than a component of it.
Using DevSecOps to Integrate Security Into the Application Lifecycle

In order to reduce product bottlenecks, DevOps was created to enhance communication between development and operational or delivery teams. By cooperating, the two teams reduce conflict and the amount of time it takes to deliver a product. But historically, it has disregarded a crucial component: security.
Security continued to be limited to QA, testing, and mostly post-delivery evaluation and patching, with minimal continuous interaction with the development team. You might be surprised to learn how bad this is.
The current regulatory landscape demands that security risks associated with applications and software be penalized more severely. 94% of CEOs want legal action taken against software companies that disregard data security, according to recent research. For this reason, it is crucial that security be included in the application lifecycle.
11 Early-Stage Security Integration Benefits
“Stronger security” is only a general, long-term justification for early security integration adoption. In the short term, DevSecOps and related methodologies are efficient for developers due to several low-hanging fruits, with little to no delivery speed trade-off.
1. Become more prepared for automation
Automated security scripts are very hard to implement after the application delivery lifecycle is finished. You can create and run security test automation scripts at important phases of the SDLC by incorporating security early on. This shortens the testing period and lowers the possibility of vulnerabilities being missed.
2. Accelerate the lifespan of application delivery
Rather than slowing down application delivery, security integration can actually accelerate it. Finding and fixing any vulnerabilities is postponed in the conventional software development life cycle (SDLC) until after all functional and non-functional criteria have been met. To make sure that other criteria are maintained, however, each fix and patch will require extensive regression testing. Large-scale product implementations typically require these essential but tedious and highly repetitive testing, which can take a significant toll on the delivery lifecycle and cause it to take much longer than anticipated to reach the market.
3. Prevent ransomware and penalties for noncompliance.
Attacks using ransomware are becoming more frequent and have the potential to pay off well. DevSecOps lowers the cost of resolving security concerns later in the development lifecycle integration by finding vulnerabilities at every step. It encourages taking a proactive stance when it comes to security, preventing costly updates and possible harm to the application’s reputation. Application developers run the danger of creating products that are vulnerable to security breaches, which might destroy consumer confidence and damage their company’s brand in the marketplace. Additionally, businesses developing applications for internal use run the risk of fines for noncompliance if client data is not adequately protected. If you invest in DevSecOps, you can mostly prevent all of this.
4. Promote uniformity to grow your development team.
Highly structured approaches such as DevSecOps, SSDLC, SecSDM, and others explicitly outline the procedures that your product team will follow, the priorities, the cooperation patterns, and the team culture. It is simpler to transition from the startup to the growth stage to maturity with this structure as it can be applied to several teams and products as you develop.
5. Confidence of external stakeholders
In addition to the obvious security benefits, avoiding circumstances where commercial demands lead you to purposefully deploy dangerous software has numerous other advantages. Your teams will operate more productively and stress-free because of the assurance that comes with understanding and conveying that security is an essential and non-negotiable component of software quality in your organization. Your developers can handle application security concerns swiftly and efficiently without compromising their work if they handle them on a regular basis as opposed to just in an emergency. The confidence of external stakeholders in your development lifecycle integration process and release schedules has increased. Furthermore, depending on your business, it could be a regulatory obligation to show that you regularly check for security flaws and never intentionally distribute insecure software.
6. Constant Watchfulness
These integrated security-by-design systems are notable for their capacity to offer 24-hour monitoring without being hampered by human weariness. Robots continuously monitor assets, deterring illegal activity and quickly spotting any dangers, which improves deterrence and early threat detection.
7. Easier and faster solutions
Dealing with other people’s code is a significant obstacle for engineers. They must first comprehend the code if they are expected to fix or modify code that they did not develop. It is still a challenging undertaking, even if contemporary development teams adhere to established procedures and coding standards to make it easier.
For this reason, developing new features or expanding on already-written code makes most developers far happier than fixing bugs. Things grow worse when the problem is with application security (including online security), as you have to comprehend not just someone else’s code but also the security flaw, which might take a lot of investigation.
8. Reducing Increasing Security Expenses
Integrated security solutions save expenses by automating processes that now call for human involvement. They provide long-term security solutions by reducing labor-intensive procedures.
9. Early detection, early correction
The likelihood of such a situation is significantly reduced with early security testing in the SDLC. The majority of vulnerabilities will be discovered well in advance of the application’s first launch. Because the complete program may be tested on an actual web server setting, some less serious flaws can also be discovered there; however, they are unlikely to have a significant impact on release dates. In the event that only low-risk flaws are automatically found, you can even configure your early testing to pass.
10. Permit cross- and upskilling among developers
DevSecOps, in the end, liberates software engineers, programmers, and developers from tightly confined silos. In an integrated security-by-design paradigm, knowing a language or being acquainted with the codebase of a product or feature is insufficient. The concerned team has to have a broad awareness of the product’s real-world functionality, security implications, and all the best and worst-case situations in the market. This will eventually result in a development staff that is both upskilled and cross-skilled, envied by your competitors, and a powerful employer brand that draws in the best coding talent.
11. Steer Clear of Intentional Exposure
It goes without saying that there might be severe consequences associated with making software vulnerable to public use. The risk of purposefully deploying software that is susceptible is entirely eliminated by early testing. Although certain vulnerabilities that were overlooked by automated scans could be found through extra manual penetration tests and staging-level testing, there is extremely little chance that these vulnerabilities will be dangerous.
One major advantage is that there is no need to deploy insecure software on purpose. Avoiding such circumstances does, however, provide several additional, specific advantages. The group need not be concerned about issues coming to light at the last minute and necessitating urgent choices. Stakeholders that depend on the software and procedure for quality maintenance include top management and outside clients. Moreover, Your company’s compliance may be impacted if it has to decide between purposefully revealing a vulnerability or postponing important feature updates.
How to Put Security Into the SDLC

Every step of the software development lifecycle integration has security-related activities incorporated, thanks to a secure software development life cycle (SDLC). Penetration testing, numerous code reviews, and architecture analysis are a few examples of such tasks. By doing this, risks are minimized or completely removed, ensuring the integrity of the finished product.
Step 1: Include Security Frameworks Based on Industry Standards
As early as the planning requirements phase, this ought to take place. As soon as you make the decision to develop a new application, your SDLC must include a reliable security model. This will include security design best practices and concepts in every step of the software development methodology you have chosen.
Step 2: Set Up a Risk Management Procedure
You must locate and adopt a second industry-standard model, one for risk management and mitigation after you’ve successfully integrated a workable security framework into your current SDLC approach. Professional techniques known as risk management processes are capable of identifying and evaluating the biggest threats to your software. They also produce matching mitigation strategies to manage and neutralize these dangers after confirmed identification.
Step 3: Put Architecture Reviews into Practice
An architecture review is a thorough examination and evaluation of the software’s layout. It is a laborious procedure that must take place in the Design stage as it would not be economical or time-efficient to determine and redesign the app at a later level.
Step 4: Phase of maintenance
It’s crucial to think about using regular security audits of all crucial apps and controls in order to preserve the strong security posture that has been developed. Although an application’s security is sufficient at present, new threats are always emerging that might compromise it. Network security provides a layer of defense and protection, but vulnerabilities in software applications, insider breaches, and insufficient security still affect sensitive systems and sensitive data.
Conclusion
In conclusion, it is critical to incorporate security concepts at every stage of the software development lifecycle integration. In addition to enabling quicker, safer delivery and the early detection and mitigation of weaknesses, it also contributes to the preservation of client confidence and a solid, trustworthy reputation.
Share this post:
Read More
- All
- AI
- AR
- DevOps and CI/CD
- E-commerce
- FinTech
- IoT
- Mobile Development
- Outstaffing
- Security
- SEO
- Tech Trends
- Web Design
- Web Development




